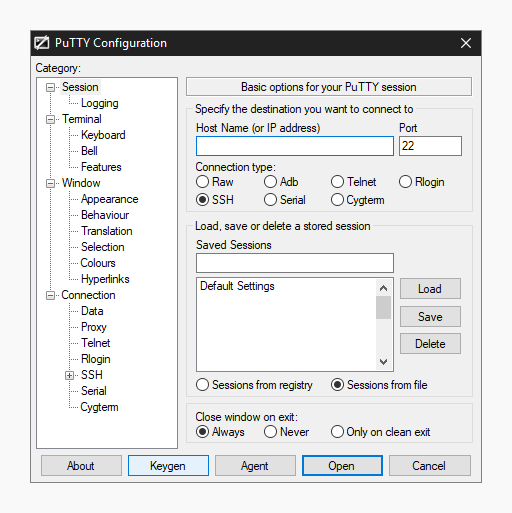
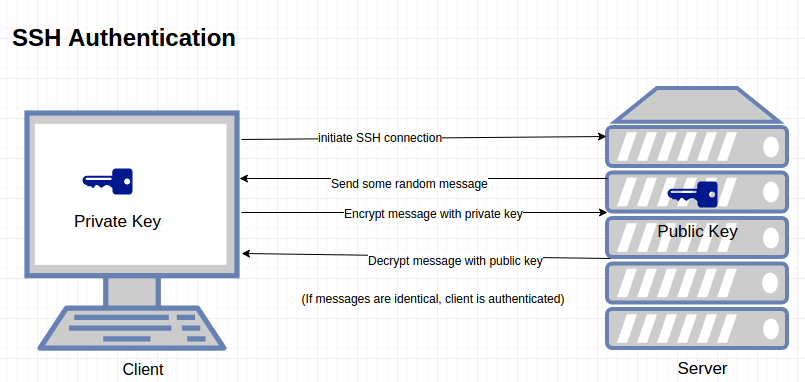
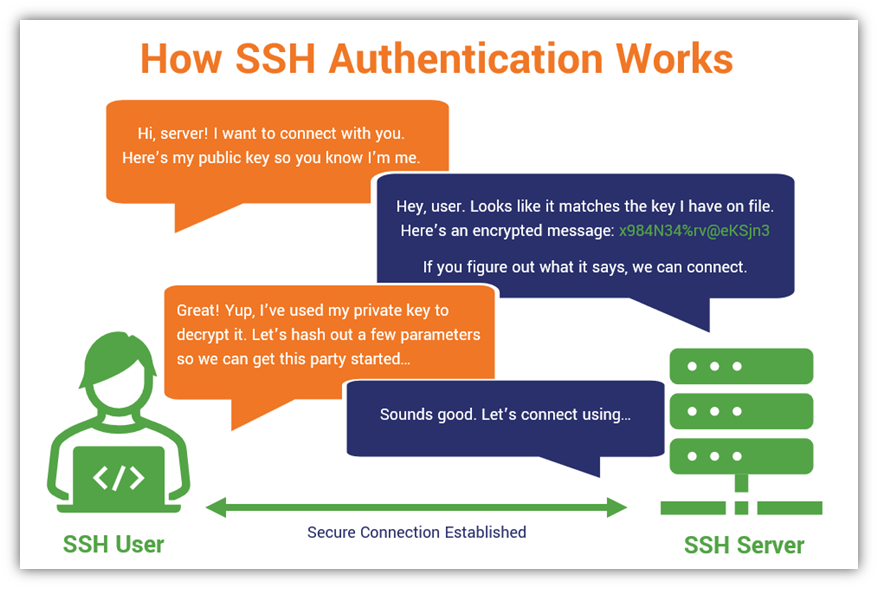
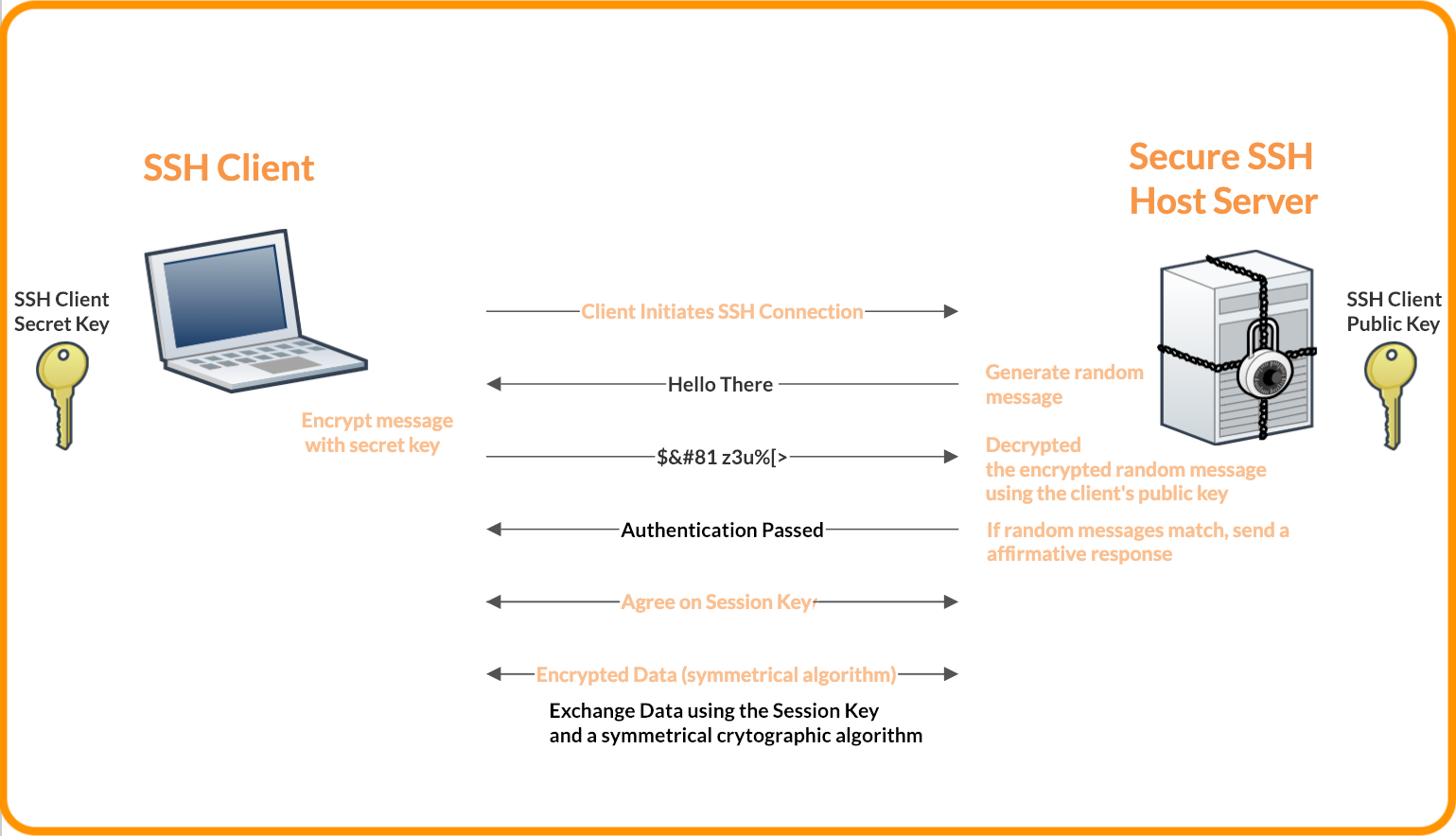
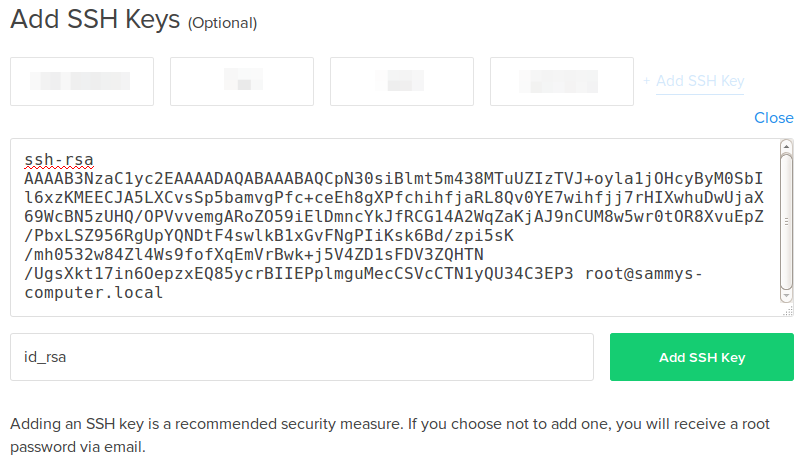
SSH keys authenticate users and hosts in SSH. They are used for single sign-on and machine-to-machine access. Security and convenience!
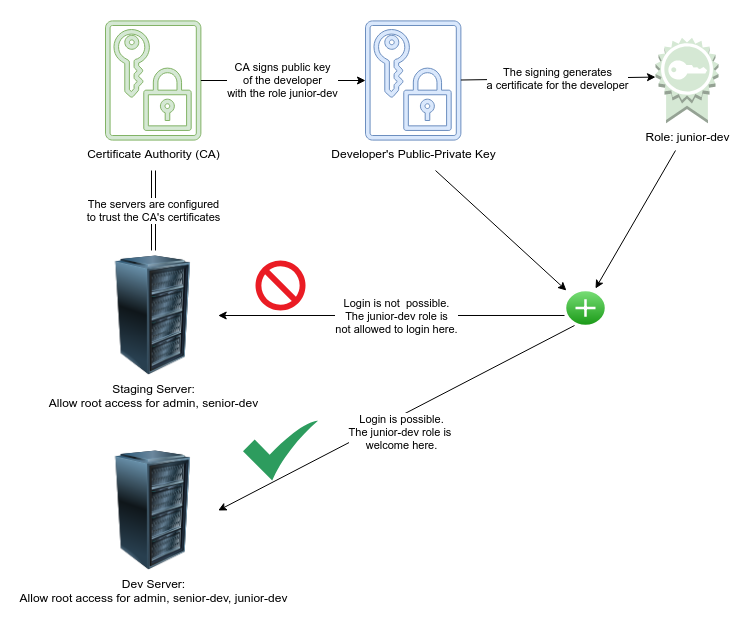
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples

privacy - Best Practice: ”separate ssh-key per host and user“ vs. ”one ssh- key for all hosts“ - Information Security Stack Exchange
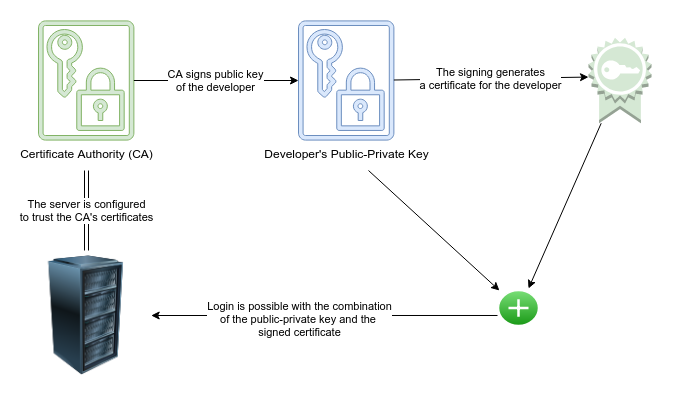



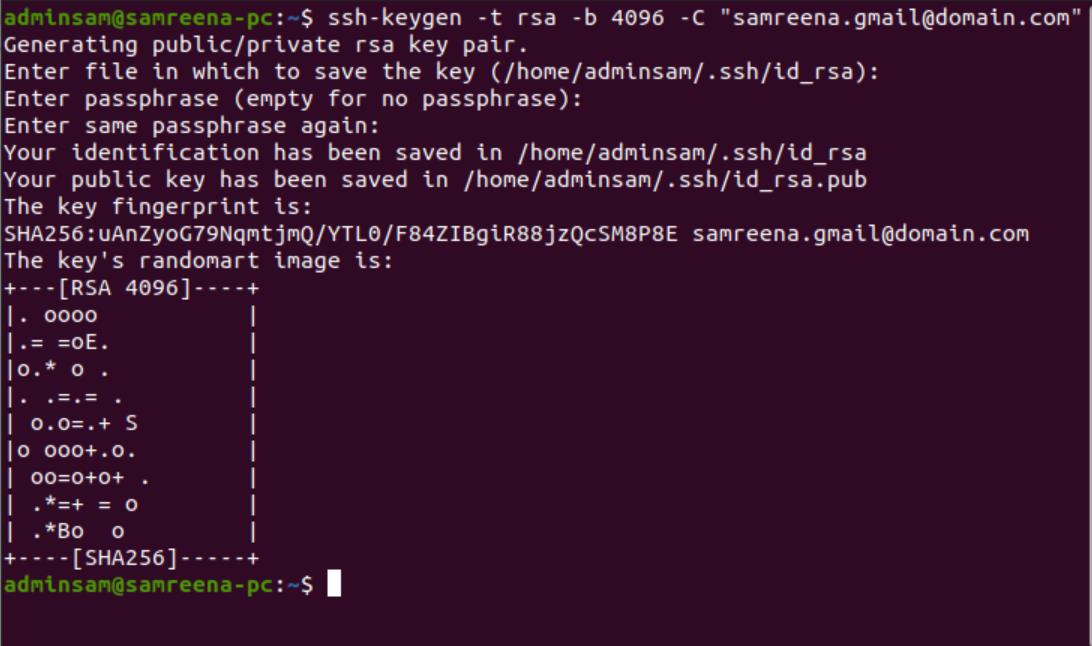

![How to SSH Through Bastion With Key [Tutorial] | strongDM How to SSH Through Bastion With Key [Tutorial] | strongDM](https://assets-global.website-files.com/5f1c75e63b2f950eb473d3e4/605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key.jpg)